In order to sue an end user,
someone they don't have a contract with, SCO has to prove that
the end user is infringing. How can they get to their target? The
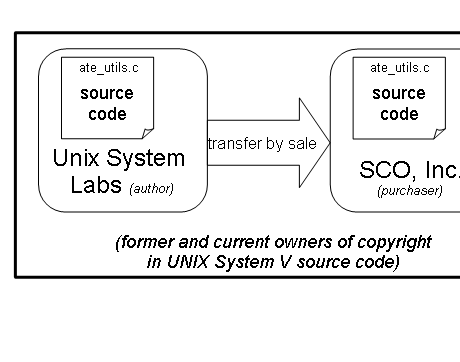
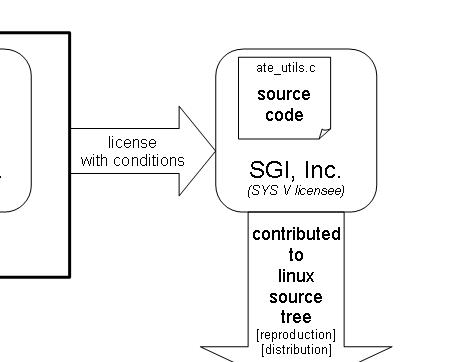
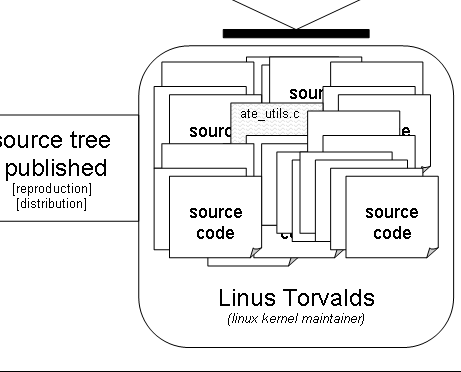
diagram below tracks SCO's claimed source code from its original
authors, through contract transfers, licenses, unauthorized copying
into the Linux kernel tree, and finally into the hands of a well-known
vendor of Linux distributions.
Each quadrant of the graphic below is linked to a page of text that
both describes the "action" within the quadrant and provides some
answers to common questions.
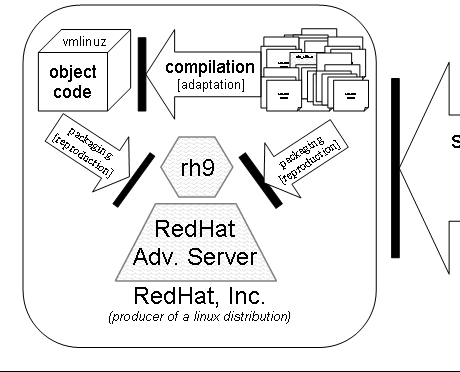
At the last link on this page, the misappropriated code has been
included in two separate Linux distributions, one called "rh9" and one
called "RedHat Advanced Server" (RHAS). But it's still not in the hands
of an end user. Stay tuned, though - that comes next.